How to Install Squid Proxy on Ubuntu 24.04/22.04 Server
Build your own caching solution for your local network with Squid and Ubuntu server. Implementing Squid as caching solutions will save your bandwidth and speed up client connections.
Squid proxy is feature-rich caching solution for HTTP, HTTPS, FTP, and transparent proxy. It also provides proxy authentication and ACLs (Access Control Lists).
In this guide. you’re going to learn how to install Squid proxy on the Ubuntu 24.04 server “Noble Numbat“. You will set up HTTPS Squid proxy via ssl_bump and enable Squid authentication via the basic_ncsa_auth module.
Prerequisites
Ensure you’ve gathered the following for this guide:
- An Ubuntu 24.04 server.
See more: How to Install Ubuntu 24.04 LTS Server - A non-root user with
sudoorrootprivileges. - A client machine – Windows/Linux/MacOS.
Installing Squid on Ubuntu
Squid is a web proxy cache for minimizing bandwidth speeding up your network speed. It is available for Unix and Linux operating systems, you can install Squid via package manager.
To install Squid on Ubuntu, carry out these steps:
1. To get started, run the apt command below to update the Ubuntu repository and get the latest package index.
sudo apt update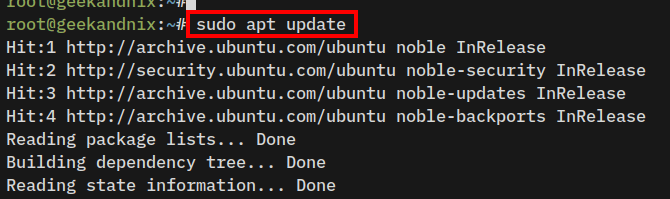
2. Install squid-openssl using the following command. Input Y to proceed with the installation. The squid-openssl package supports ssl-bump feature for creating HTTPS proxy.
sudo apt install squid-openssl squidclient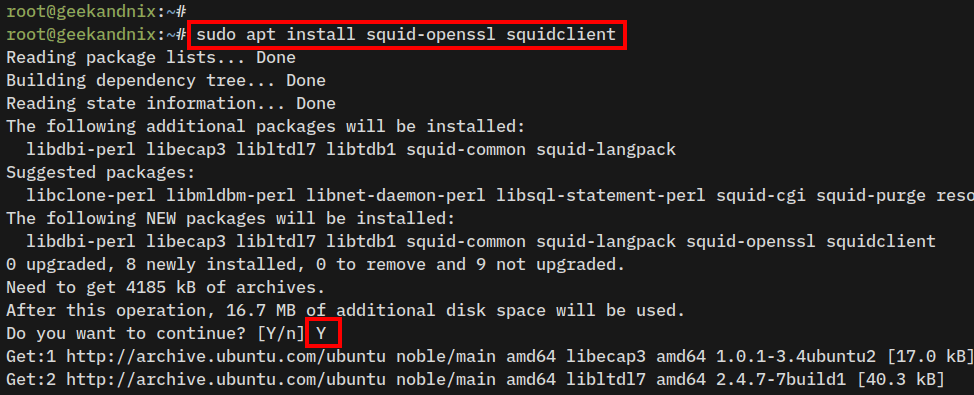
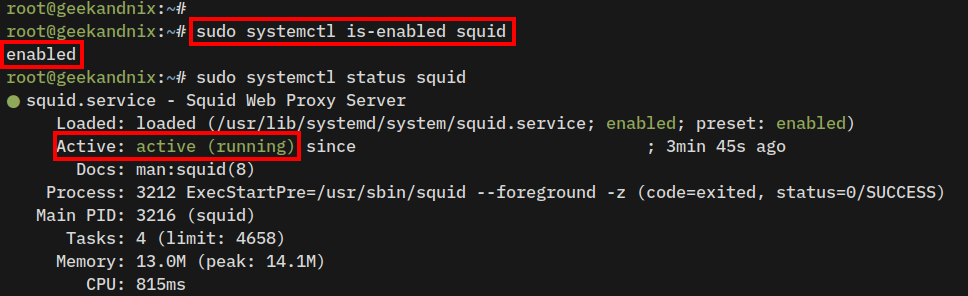
3. After you’ve installed squid, the squid service will start and be enabled automatically on your server.
Run the following command to check the squid service status.
sudo systemctl is-enabled squid
sudo systemctl status squidWhen squid is running, you will see the output active (running). The output enabled confirms squid will start automatically on system boot.
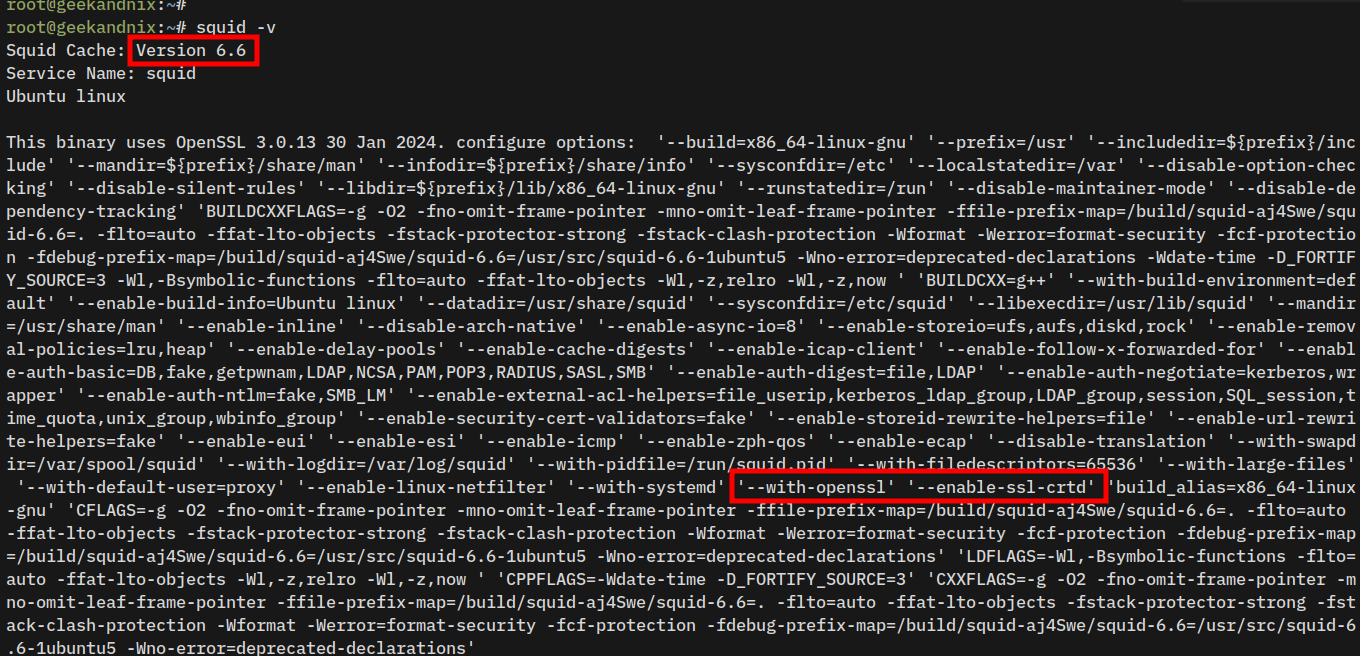
4. Lastly, verify the details of Squid version using the command below.
squid -vEnsure the build parameter --with-openssl and --enable-ssl-crtd is available. Those two parameters allow you to create an HTTPS Proxy with Squid.
Squid Configuration Files and Directory
Before configuring squid, familiarize yourself with the squid configuration files and directories below:
- squid.service: This service file for squid is located in the
/usr/lib/systemd/system/directory. - /etc/squid: Configuration directory where
squid.conf– main squid configuration is stored. - /var/spool/squid: The default cache directory for squid.
- /var/log/squid: The log directory for squid. Check the
access.logto debug squid andcache.logto get detailed squid cache information.
Generating Self-Signed SSL/TLS Certificates
In this section, you will generate new self-signed SSL/TLS certificates for creating a squid HTTPS proxy on your Ubuntu server.
Perform these actions to generate Self-Signed SSL/TLS certificates:
1. Execute the following command to create a new directory /etc/squid/cert/ and move into it.
mkdir -p /etc/squid/cert; cd /etc/squid/cert/2. Generate Self-Signed TLS certificates using the openssl command below. You will generate two keys squid-ca.key and squid-ca.crt.
openssl req -new -newkey rsa:2048 -days 365 -nodes -x509 -extensions v3_ca -keyout squid-ca.key -out squid-ca.crt3. Now, run the command below to convert the squid-ca.crt to .PEM format squid-ca.pem. The certificate file squid-ca.pem will be used by the client browser.
openssl x509 -in squid-ca.crt -outform PEM -out squid-ca.pem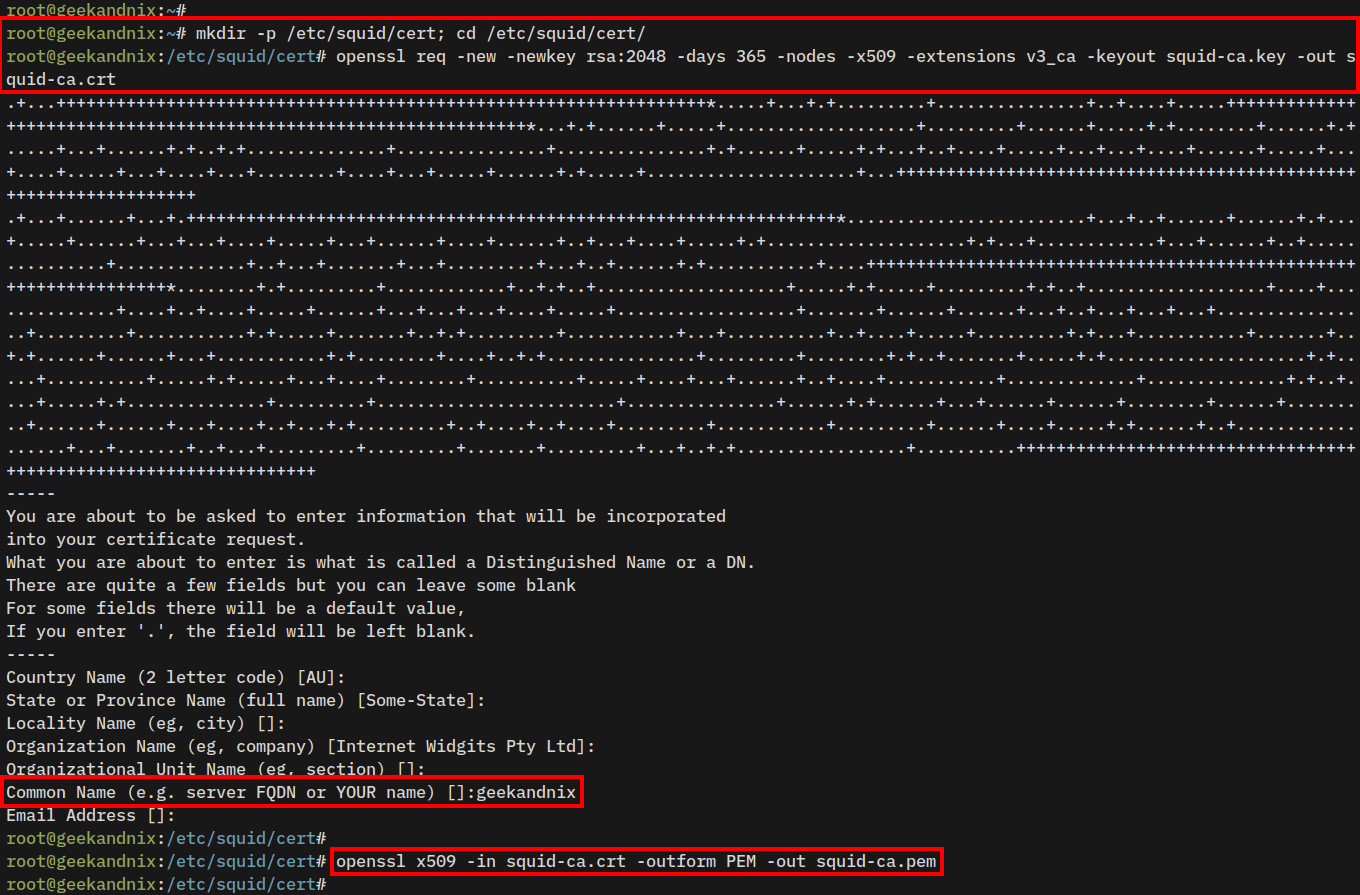
4. Next, run the command below to generate the DHPARAM certificate squid-ca-dhparam.pem.
openssl dhparam -outform PEM -out squid-ca-dhparam.pem 2048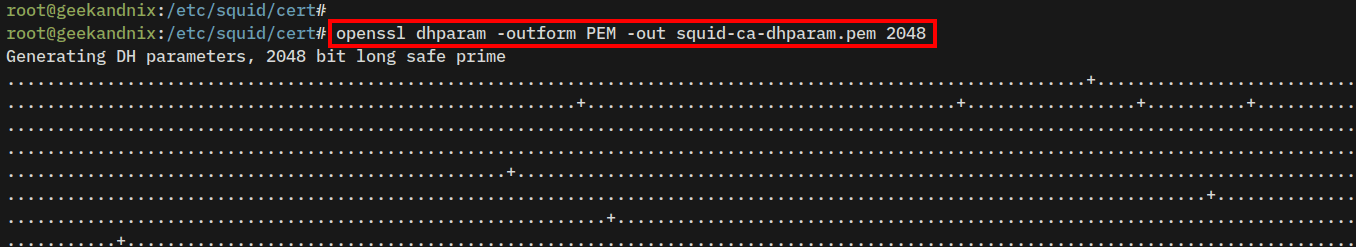
5. After that, change the ownership of the /etc/squid/cert directory to the user proxy.
sudo chown -R proxy /etc/squid/cert6. Lastly, run the following command to initialize the certificate database for squid.
sudo -u proxy /usr/lib/squid/security_file_certgen -c -s /var/spool/squid/ssl_db -M 32MB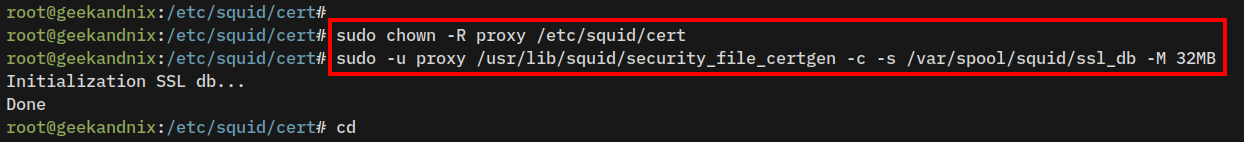
Configuring Squid HTTPS Proxy on Ubuntu
Now that you’ve installed Squid and generated SSL/TLS certificates, you’re ready to create an HTTPS proxy server with Squid. The squid HTTPS proxy server will be able to cache both HTTP and HTTPS requests from the client.
To configure Squid as a HTTPS proxy, execute these steps:
1. First, backup the squid configuration to /etc/squid/squid.conf.orig and open the file /etc/squid/squid.conf using vim.
cp /etc/squid/squid.conf /etc/squid/squid.conf.orig
sudo vim /etc/squid/squid.conf2. Find the http_port line, and input your internal IP address and the port for squid.
In this case, squid will be run at 192.168.5.65 with default port 3128 and enable the ssl_bump feature to set up HTTPS proxy.
# Squid normally listens to port 3128
http_port 192.168.5.65:3128 ssl-bump generate-host-certificates=on tls-cert=/etc/squid/cert/squid-ca.crt tls-key=/etc/squid/cert/squid-ca.key tls-dh=/etc/squid/cert/squid-ca-dhparam.pem3. Insert the following configuration to enable bumping for intercepting HTTPS connections.
# New with peek and bump
# enable ssl_bump
acl step1 at_step SslBump1
ssl_bump peek step1
ssl_bump bump all
# setup sslcrtd_program
sslcrtd_program /usr/lib/squid/security_file_certgen -s /var/spool/squid/ssl_db -M 32MB
sslcrtd_children 5
ssl_bump server-first all
sslproxy_cert_error allow allAlternatively to that, you can use the below configuration:
# setup sslcrtd_program
sslcrtd_program /usr/lib/squid/security_file_certgen -s /var/spool/squid/ssl_db -M 32MB
sslcrtd_children 5
# enable ssl_bump
ssl_bump server-first all
ssl_bump stare all4. Next, uncomment the cache_dir option to enable squid cache via disk. Tune up the default configuration with the following:
cache_dir ufs /var/spool/squid 3000 16 256 max-size=200000000Save the file and exit the editor when finished.
Below are the detailed options for squid cache_dir:
- ufs: This is the default storage format for squid.
- /var/spool/squid: Target directory where squid cache will be stored.
- 3000: Set up the total cache size max to 3000MB or 3GB.
- 16: The default first level of sub-directories for squid cache is 16.
- 256: The second level of sub-directories for squid cache will be 256.
- max-size: Set up the max cached file size will be 200000000 bytes or 20GB.
5. Next, run the vim command below to create a new ACL (Access Control Lists) configuration for your local network.
sudo vim /etc/squid/conf.d/acl.confAdd the following configuration and be sure to change the details of the subnet with your local network subnet.
# Create ACL mynet with network 192.168.5.0/24
acl mynet src 192.168.5.0/24
# Create ACL kids_net with network 172.8.1.0/24
acl kids_net src 172.8.1.0/24
# Create ACL kids_hours type time
# Mondat-Saturday on clock 12:00-20:00
acl kids_hours time M T W T F A 12:00-20:00
# Allow mynet to access squid
http_access allow mynet
# Allow kids_net to access squid
# on kids_hours only
http_access allow kids_net kids_hoursWhen finished, save the file and exit the editor.
In this example, you will create three ACLs:
- mynet with the default source network
192.168.5.0/24. - kids_net
172.8.1.0/24. - kids_hours is the ACL type time, which specifies days
Monday-Saturdayand hours12:00-20:00.
Then, you will allow access to squid via the http_access allow parameter:
- Allow mynet to access the squid proxy.
- Allow kids_net to access squid proxy only within the kids_hours, which is Moday-Saturday on hours 12:00-20:00.
6. Now run the squid command below to verify squid configurations.
squid -k check && squid -k parseEnsure you’ve no syntax errors and the acl.conf file loaded by squid.
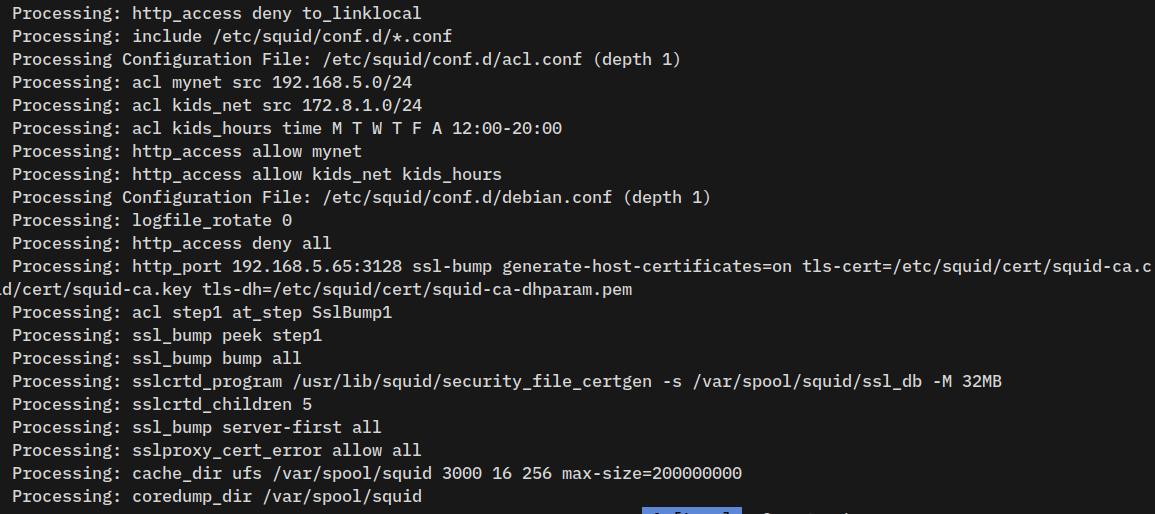
7. Lastly, run the following systemctl command to restart squid and take the effects of your changes.
sudo systemctl restart squidAdding Authentication to Squid
After configuring the squid HTTPS proxy, you will configure squid authentication via the squid basic_ncsa_auth module.
To set up squid authentication, complete these tasks:
1. First, generate the password file /etc/squid/htpasswd using the following command. Be sure to change the user geekandnix and the password secretpass.
printf "geekandnix:$(openssl passwd -apr1 secretpass)\n" | sudo tee -a /etc/squid/htpasswd2. Open the custom ACL configuration /etc/squid/conf.d/acl.conf using vim.
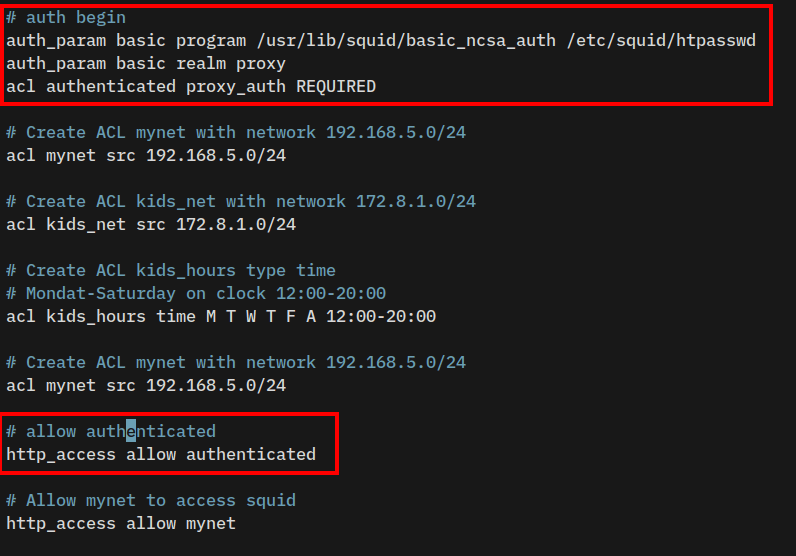
sudo vim /etc/squid/conf.d/acl.conf3. Put the following configuration in before the parameter acl mynet src 192.168.5.0/24.
# authentication begin
auth_param basic program /usr/lib/squid/basic_ncsa_auth /etc/squid/htpasswd
auth_param basic realm proxy
acl authenticated proxy_auth REQUIRED
# Create ACL mynet with network 192.168.5.0/24
acl mynet src 192.168.5.0/244. Insert the following configuration before the http_access allow mynet parameter.
# allow authenticated user
http_access allow authenticated
# Allow mynet to access squid
http_access allow mynetSave the file and exit the editor when you’re done.
4. Now, run the command below to verify the squid configuration. Ensure the new configuration is loaded.
squid -k check && squid -k parse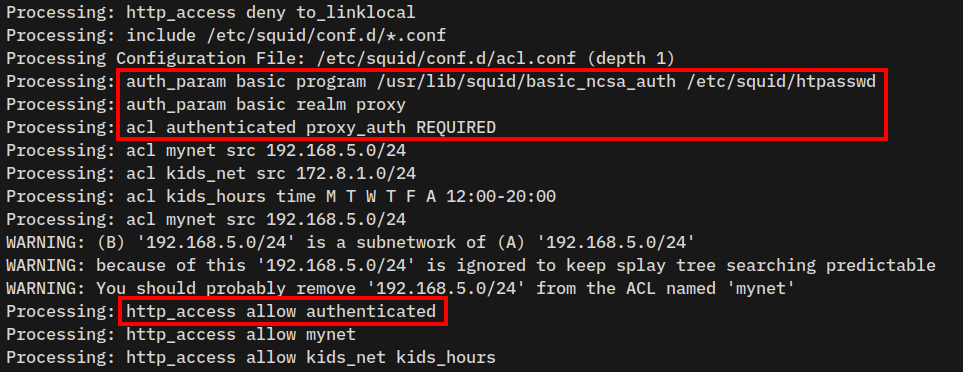
5. Lastly, restart the squid service using the following command to apply your changes.
sudo systemctl restart squidConfiguring UFW (Uncomplicated Firewall)
Now that you’ve configured the squid HTTPS proxy and enabled the authentication, you can proceed to configure UFW (Uncomplicated Firewall) and allow traffic to squid port 3128.
See more: Master the UFW Firewall on Ubuntu: 17 Practical Examples
1. Execute the ufw command below to open squid http port 3128. Change the following subnet with your local networks.
sudo ufw allow from 192.168.5.0/24 to any port 3128
sudo ufw allow from 172.8.1.0/16 to any port 31282. Then, verify UFW using the following command.
sudo ufw status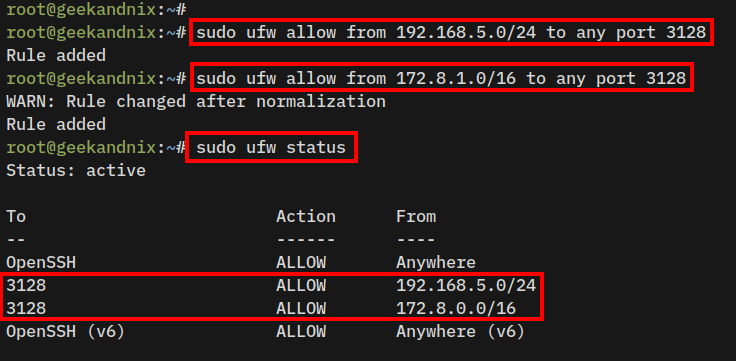
Connecting to Squid from Client Machine
At this point, you have completed the squid proxy installation, it’s time to verify squid from the client machine. In this example, we’ll be using a Windows client machine with the Mozilla Firefox browser.
Complete these actions to connect to the squid HTTPS proxy server:
1. First, you must copy the certificate file squid-ca.pem from the squid server to your client machine. use the following scp command to achieve that.
scp [email protected]:/etc/squid/cert/squid-ca.pem .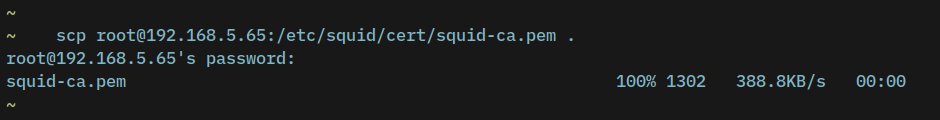
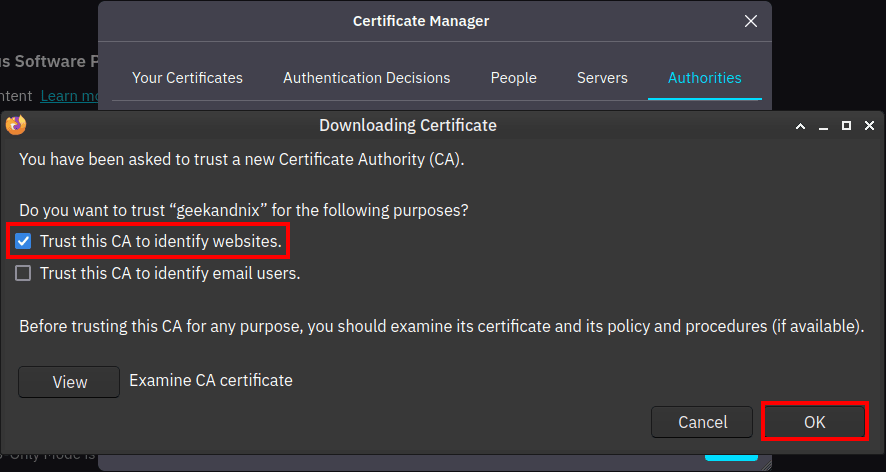
2. Open your web browser and import the squid-ca.pem certificate file. Below is an example for a Firefox user.
- Click Settings > Privacy & Security.
- On the Security > Certificates > View Certificates.
- Click Import, check the option Trust this CA to identify websites, then click OK to confirm.
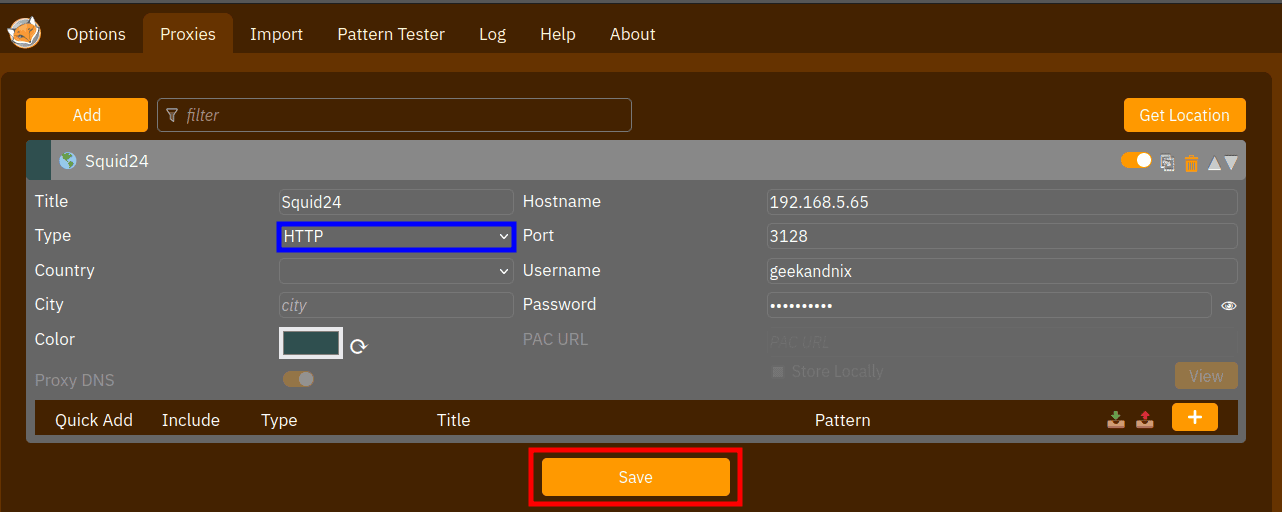
3. Now, install FoxyProxy extension via https://addons.mozilla.org/. Then, create a new proxy with the configuration like this:
Be sure to change the Proxy Type as HTTP, then input the IP address and user password for the squid proxy server.
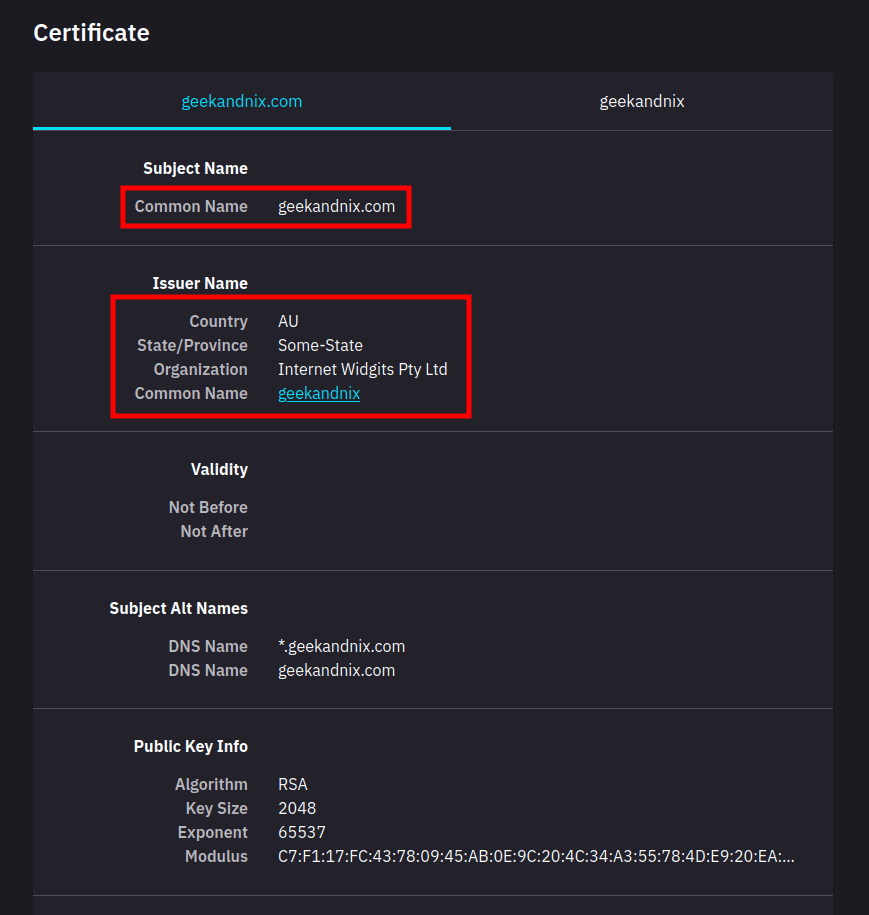
4. Once you’ve activated the proxy, visit any sites with HTTPS protocol, such as https://geekandnix.com/. Then, click on the lock HTTPS icon to get information about the current SSL certificates.
Click View Certificates.
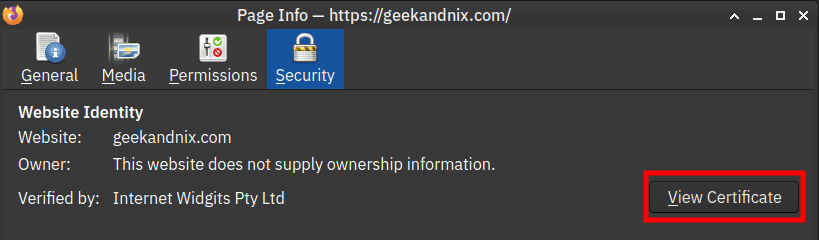
5. If your installation is successful, you should get the certificate of squid proxy, instead of the certificate for geekandnix.com.
Managing Squid Service
This section shows you how to manage the squid service via the systemd systemctl utility.
1. To start squid, run the following systemctl command.
sudo systemctl start squid2. Now, if you want to stop squid, use the command below.
sudo systemctl stop squid3. After making changes to squid, apply your changes by executing the following.
sudo systemctl restart squid4. Next, verify the squid service status using the command below.
If squid is running, you will see an output active (running). Also, you will see the output enabled, which confirms that squid will start automatically at boot.
sudo systemctl status squid5. Lastly, if the squid service is disabled, run the command below to enable it.
sudo systemctl enable squidHow do I Know if Squid Proxy is Working?
To verify if Squid is working, do these actions:
Simple Check via tail command
To check if the squid working or not, you must check the squid log file /var/log/squid/access.log using the tail command below.
sudo tail -f /var/log/squid/access.logYou will see the squid log files, below is an example:
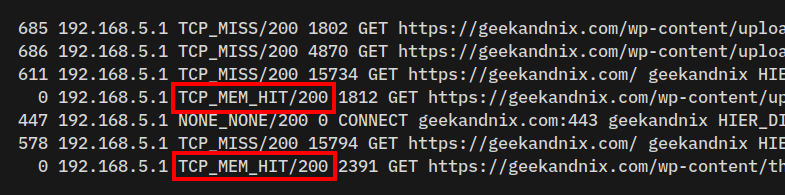
The TCP_MEM_HIT/200 means the client got the data from squid caches stored in RAM memory.
Generating Squid Report via Calamaris
1. First, run the apt command below to install the calamaris package.
sudo apt install calamaris
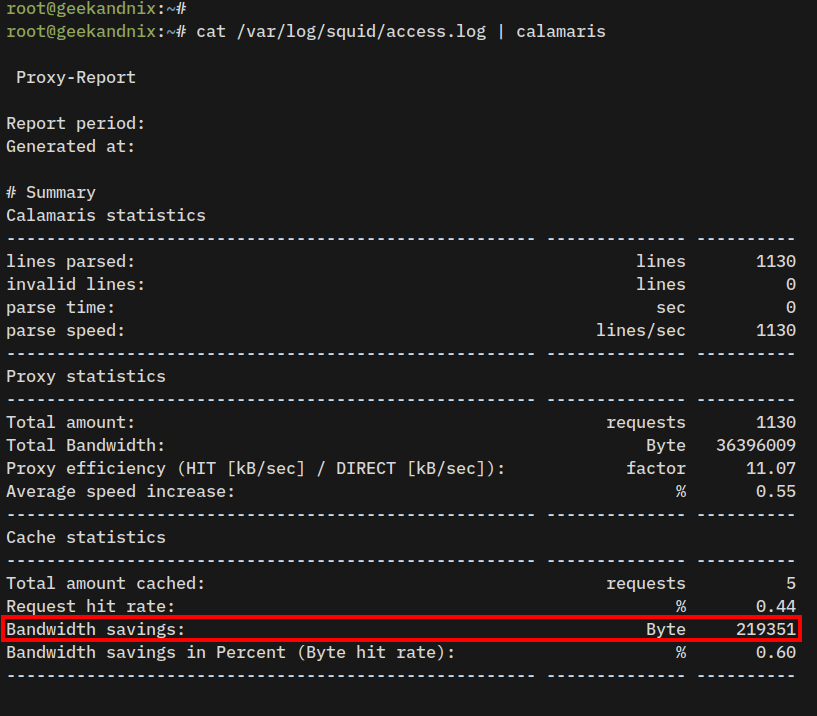
2. Now run the command below to generate report from Squid access log /var/log/squid/access.log.
cat /var/log/squid/access.log | calamarisWithin the Cache statistics section, you can see how much HIT rate and Bandwidth savings by Squid.
Basic Debugging Squid Proxy
When an error occurs on squid, take these actions to debug your squid proxy installation:
1. First, ensure that the squid service is running by executing the command below.
sudo systemctl status squid2. If squid is running and you still can’t access it, check squid port 3128 to ensure that port 3128 is not blocked by the firewall.
nc -zv 192.168.5.65 3128
3. Lastly, be sure to check the squid error log /var/log/squid/error.log using the tail command below.
sudo tail -f /var/log/squid/error.logUninstalling/Removing Squid
1. Before uninstalling squid, stop and disable the service using the following command.
sudo systemctl disable --now squid2. Now, remove the squid package using the apt command below.
sudo apt purge squid3. Lastly, remove squid configuration files and directory using the following command.
sudo rm -rf /var/spool/squid /etc/squidConclusion
Congratulations! You’ve installed Squid and configured HTTPS Proxy on the Ubuntu 24.04 server. You’ve also enabled Squid authentication and secured Squid with UFW (Uncomplicated Firewall).
Moreover, you’ve also learned how to connect to the Squid HTTPS proxy from the client machine using FoxyProxy browser add-ons.
At this stage, you may also configure Squid as Transparent Proxy or “forced proxy” for your clients.